Replace MIM with cloud-first hybrid
Following James’ insightful webinar on Microsoft Entra cloud-first IAM, I’d like to take a closer look at moving away from Microsoft Identity Manager (MIM) and transitioning to cloud-first provisioning.
Current implementation
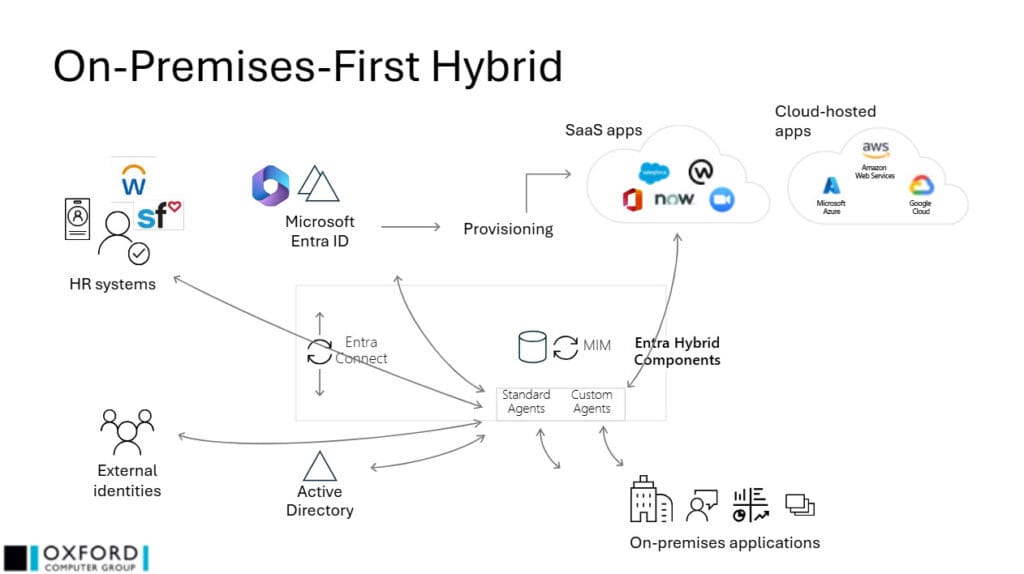
If you are using MIM today, your setup is likely to resemble this diagram:
MIM imports data from at least one HR source, provisions to on-premises applications (including Active Directory (AD)) and possibly handles some Microsoft Entra ID accounts. Microsoft Entra Connect or Cloud Sync likely manages the AD objects in Microsoft Entra ID.
We recommend taking a phased approach to move your implementation to cloud-first.
1. Move provisioning from HR sources directly into Microsoft Entra ID
Your first goal should be provisioning from HR systems directly into Microsoft Entra ID, with MIM continuing to manage on-premises applications (as shown in the diagram below). For complex environments with multiple HR sources, pre-import consolidation using Azure Data Factory may be necessary.
As an interim step, MIM can handle bulk provisioning into Microsoft Entra ID using the bulk provisioning endpoint before transitioning to Azure Data Factory or Logic Apps (Oxford Computer Group has a Proof of Concept( PoC) and MIM management agent to do just this – contact us for more details).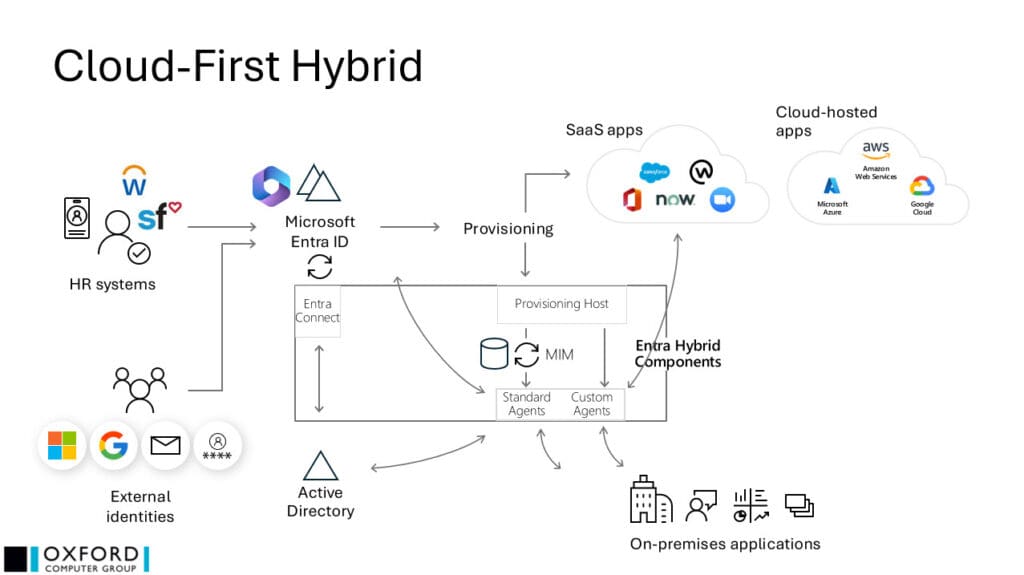
An immediate benefit is that cloud-only accounts (i.e. those without an AD account) can be managed directly in Microsoft Entra ID, allowing them to be removed from MIM.
As many organizations aren’t ready to remove AD yet, this method assumes provisioning to AD will remain – either through MIM or from Microsoft Entra ID directly (either to start with or later in the migration journey).
2. Replacing MIM HR management agents
Once accounts are provisioned into Microsoft Entra ID, they must be integrated with MIM for on-premises application provisioning. This integration relies on the on-premises Provisioning Agent and Extension Connectivity (ECMA) Connector Host.
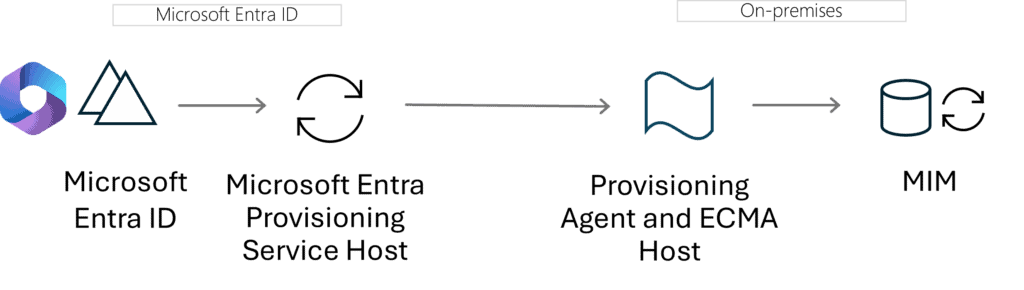
The provisioning agent ensures secure connectivity between Microsoft Entra ID and your on-premises environment. The ECMA host connector converts provisioning requests from Microsoft Entra ID into actions that MIM can process. If many HR attributes are imported into MIM, some re-organization may be needed, as only a fixed number of attributes are available to use in Microsoft Entra ID.
You can provision MIM through the MIM Service (Portal) or a Microsoft SQL staging table.
Provisioning agent
The first step to set up provisioning to MIM from Microsoft Entra ID is to install the provisioning agent and ECMA host. This combined install can be done on any suitable server with network connectivity to Microsoft Entra ID, though installing it on the MIM server is often more convenient. The setup is straightforward and registers the agent with Microsoft Entra ID.
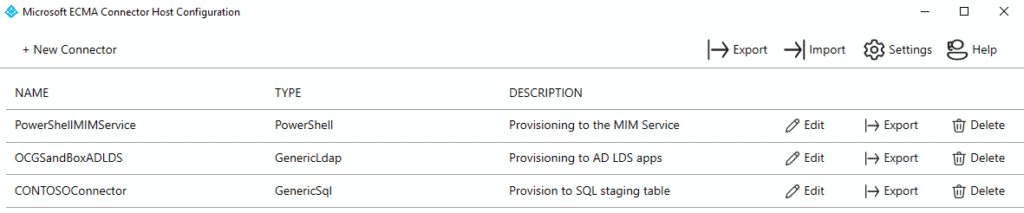
Next, you’ll configure the connector. The following screenshot is an example of connectors set up to provision to the MIM Service (via PowerShell), an AD LDS-based application, and to a SQL staging table:
PowerShell (MIM Portal) connector
In this scenario, a PowerShell connector provisions via the MIM Service. The open-source Lithnet Service PowerShell Module by Ryan Newington handles the import and export of user objects.
Microsoft provides documentation on how to configure a PowerShell connector but in summary:
- Write a script for schema discovery
- Add additional configuration parameters (these show up on the Global configuration page)
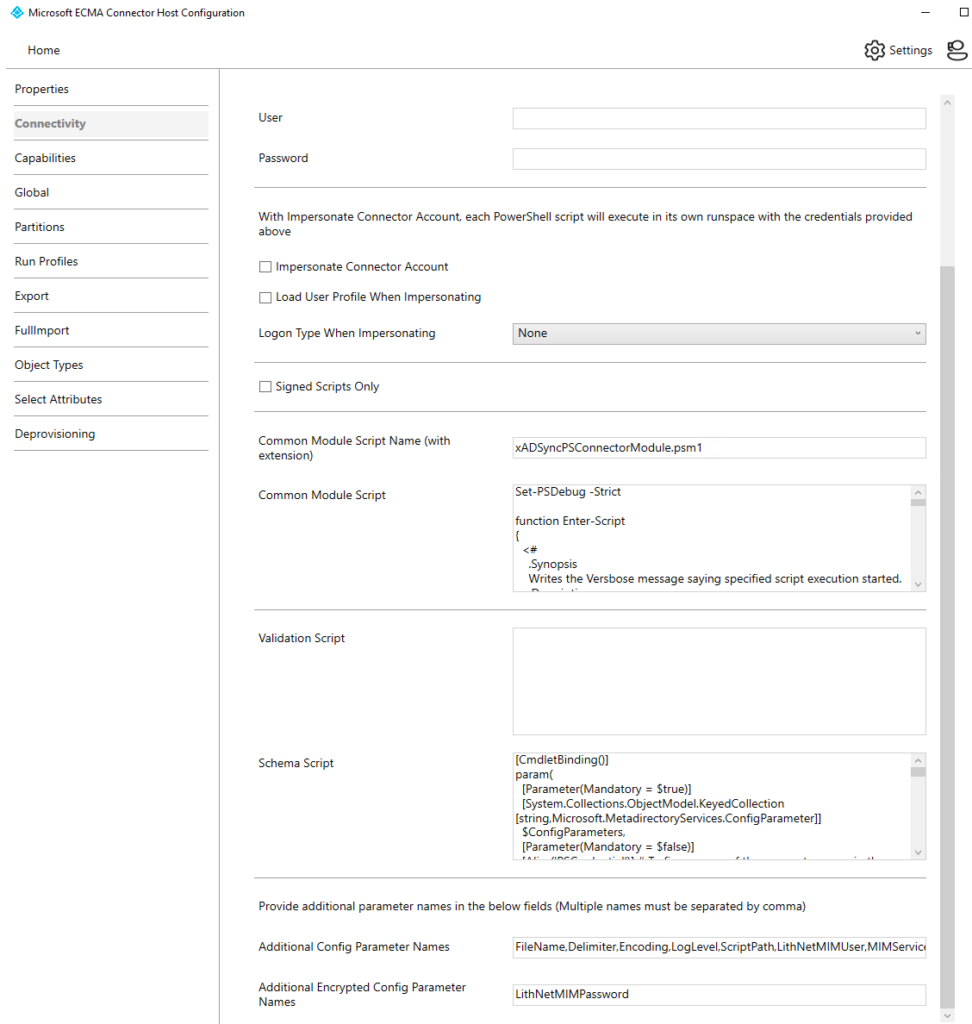
- Write a script to import the user objects from the MIM Service
- Write a script to export a user to the MIM Service
- Set necessary script parameters
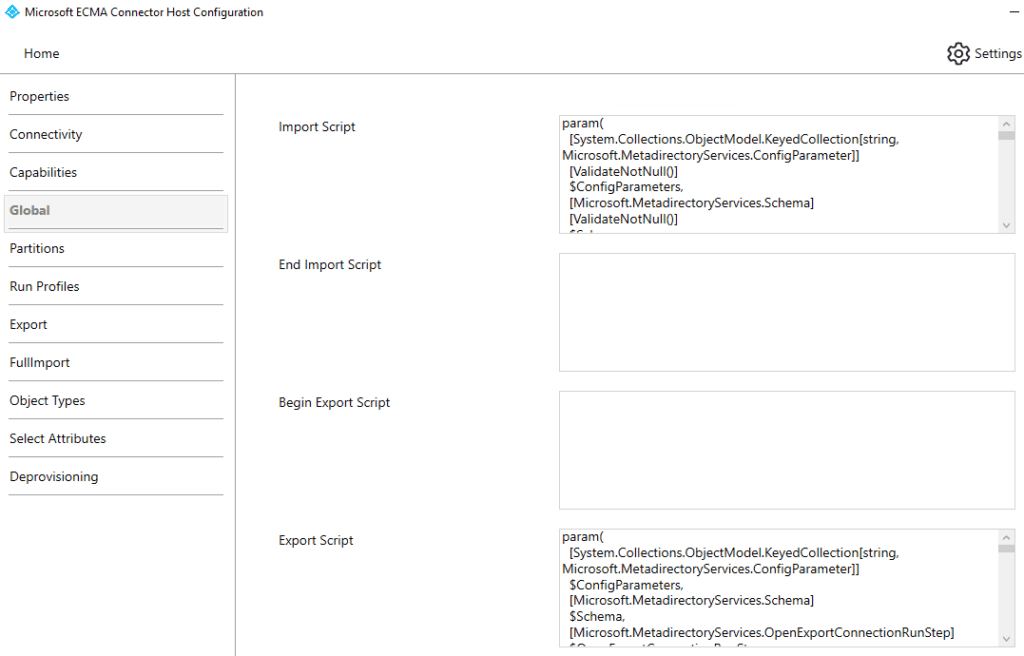
- Configure Export and Full Import Run Profiles
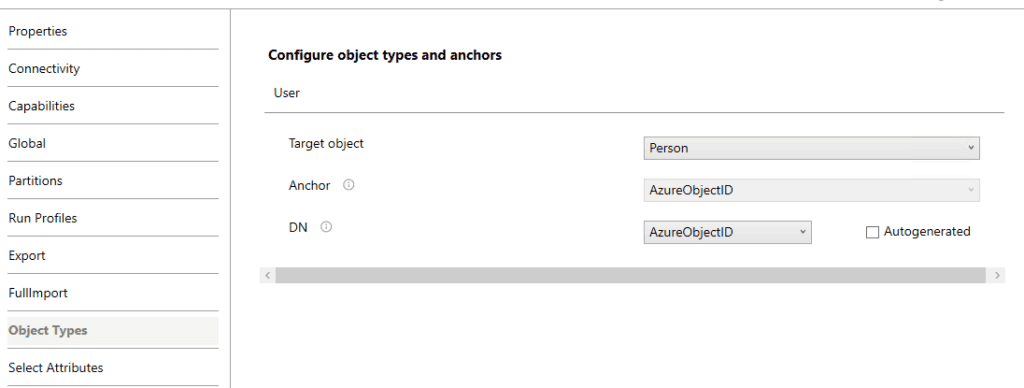
- Configure object type and attributes

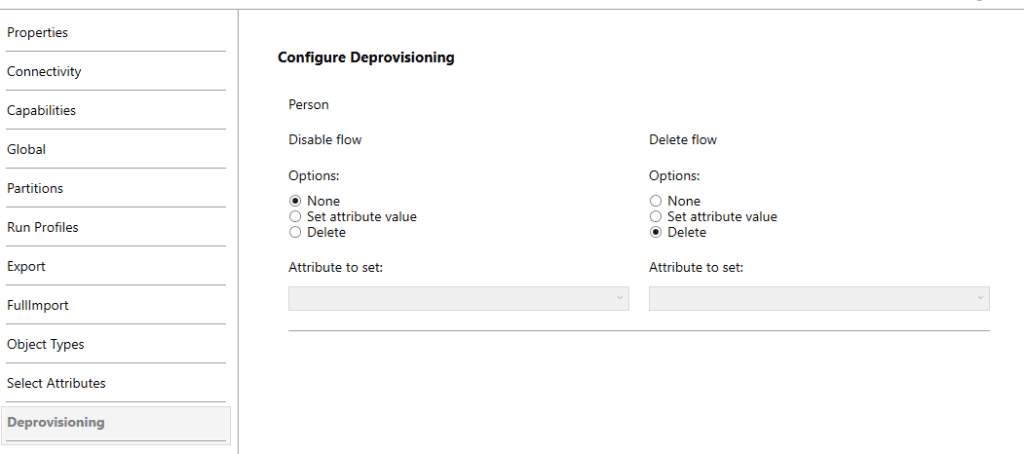
- Setup de-provisioning
SQL connector
The Generic SQL connector can provision to a Microsoft SQL staging table, which the existing MIM HR connector will be reconfigured to use rather than the HR system.
Microsoft provides documentation on how to configure the Generic SQL connector, but in summary:
- Create a DSN file with connection details
- Configure the schema (‘user’ object type, attribute type detection, anchor and DN, attribute data type)
- Set global parameters (e.g., time zone and date format)

- Configure Export and Full Import Run Profiles
- Configure object type and attributes
- Set up de-provisioning
Microsoft Entra ID provisioning application
Once the agent and connector are configured, you’ll need to tell the Entra ID’s provisioning service to use them. At a high level, the steps are:
- Create a new enterprise application (‘On-premises ECMA app’)
- Enable automatic provisioning
- Assign the agent

- Configure the connection

- Define the attribute mappings (the attributes configured in the connector should appear automatically)
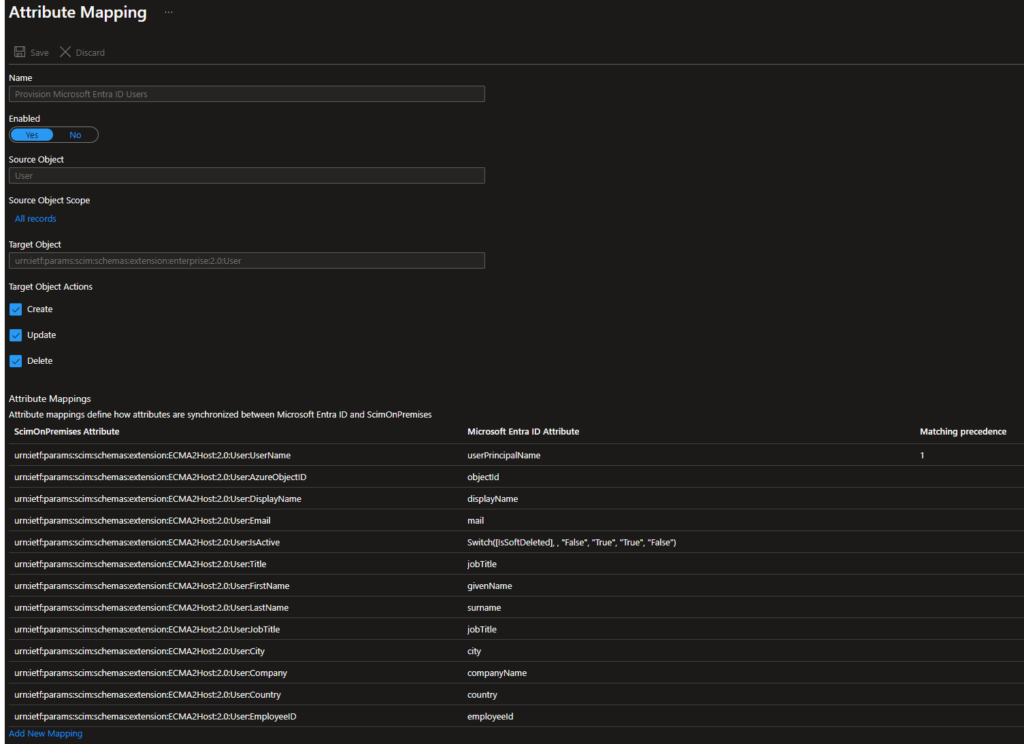
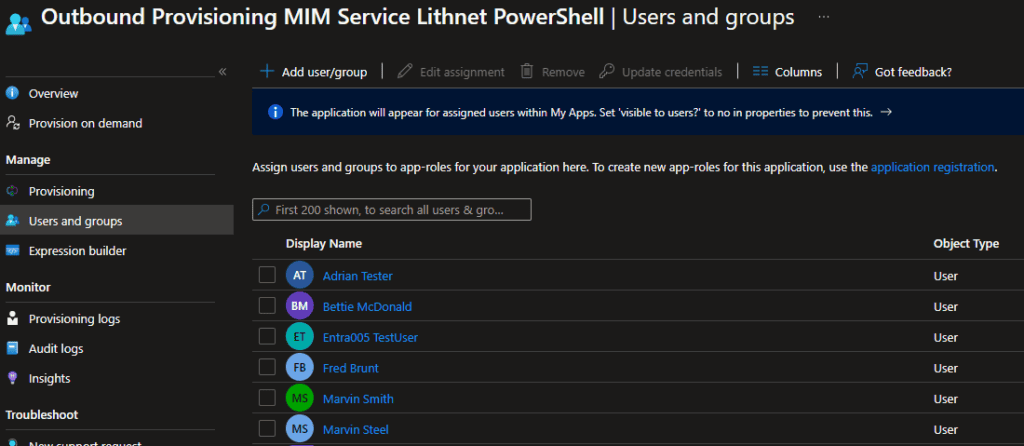
- Add a user to the scope for testing (typically changed to a group later)
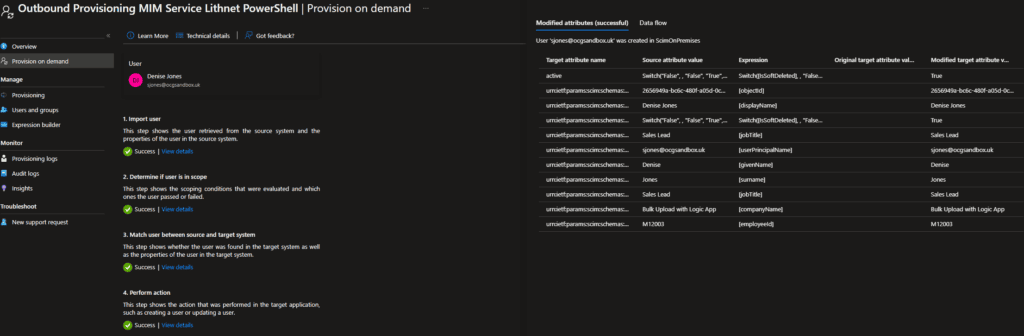
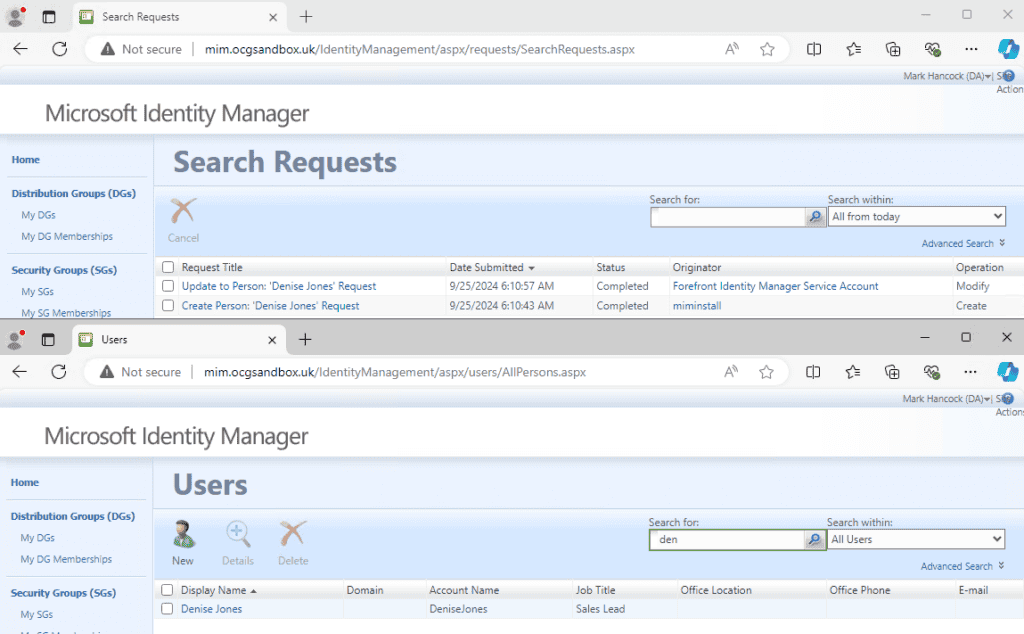
- Run tests
3. Next steps to retiring MIM
Your next steps toward retiring MIM will depend on your specific environment, but here are some common options:
- Move provisioning to on-premises apps (except AD) from MIM to the ECMA host using supported connectors (SQL, LDAP, REST/SOAP, and PowerShell). Providing certain conditions are met, any custom ECMA2 connectors from MIM can also be used
- Provision AD accounts from Microsoft Entra ID via HR or API-driven provisioning. (In the future, we hope to see Cloud Sync support for provisioning users as it does with groups)
- Migrate on-premises applications to SaaS versions where possible, provisioning directly from Microsoft Entra ID
- Use access packages to request and assign on-premises applications and permissions
Note: If MIM manages object types other than users, it will be more difficult to retire since on-premises provisioning currently only supports users (except for AD groups with Cloud Sync).
Need help?
At Oxford Computer Group, we specialize in helping clients across industry sectors move from MIM to a cloud-first identity model. With decades of experience in MIM, we understand the intricacies of user provisioning and how to navigate the transition.
- Request a MIM Migration Design Workshop. We evaluate your current setup and provide a tailored design specification report for your best migration path from MIM
- Explore our insightful articles on MIM migration
- Watch our webinar ‘Transitioning from MIM to Microsoft Entra cloud-first IAM’
- Watch our webinar ‘Moving from MIM to Microsoft Entra ID Governance’
- Talk to us about how we can support your MIM implementation, so your team can focus on the migration
- Contact us to discuss your next steps